
WhiteSource Open Source Security
Open Source Security


One of the biggest information security tragedies of all times, the Equifax breach, demonstrated the importance of open source security. As tragic as the theft of 145.9 million personally identifiable information was, it was the learning experience of “never-again” proportions that made Equifax a poster child for open source software security.
Once an open source vulnerability is reported, it becomes a ticking time bomb in your application that hackers are actively trying to infiltrate. Efficient detection and remediation are the only way to keep ahead of hackers. Investing in an automated security solution that monitors your open source inventory for vulnerabilities, while also aggregating known vulnerabilities from all bug trackers in the open source community, is the only way to achieve comprehensive and continued coverage of your open source components.
The Challenges of Open Source Security
While useful for proprietary code, application security testing technologies like SAST, cannot detect vulnerabilities in open source components. For open source security, a community based approach is needed which utilizes the open source community as the resource for detecting and fixing vulnerabilities.
The open source community does a good job securing open source projects, detecting vulnerabilities and coming up with fixes, but by its very nature open source is a decentralized operation. Data about vulnerabilities is spread out over multiple resources, making it impossible for corporations to manually match vulnerabilities listed in these dispersed listings to those in their applications.
Without transparency into their open source inventory corporations are unable to detect vulnerable components, leaving them as ticking time bombs in their source code.
Step I: Vulnerability Detection
You can’t fix what you don’t know you have. It’s that simple. WhiteSource is able to detect all vulnerable open source components in your application, including in your transitive dependencies, in over 200 programming languages.
Prioritizing Effective Vulnerabilities – WhiteSource’s Effective Usage Analysis technology adds a never before seen level of resolution for understanding which vulnerable functionalities are indeed effective (i.e. getting calls from the proprietary code). Thus, reducing open source vulnerability alerts by 70% and helping development teams prioritize the issues that truly need fixing.
The End to False Positives – Thanks to our proprietary algorithm, we match reported vulnerabilities to the actual affected open source libraries in your code, ensuring no false positive alerts that only waste your time and resources.
Comprehensive Database – Our database provides the largest coverage of vulnerability listings, with more than 200 programming languages supported and continuous monitoring of multiple vulnerability databases including the CVE/NVD, a wide range of security advisories, and popular open source projects issue trackers.
Step II: Vulnerability Remediation
If detection is the crucial first step, remediation efforts are the race to the finish line. Once a vulnerability has been published in the community issue trackers, hackers are on it and ready to exploit. To be effective, remediation efforts must therefore be timely. Remediation requires that developers and security teams work swiftly and efficiently with code they are not familiar with and did not write themselves.
Pinpointing the Path to Vulnerabilities – WhiteSource provides full trace analysis, pinpointing the vulnerable functionality in your code and mapping out the way the vulnerability is being used in your application. These actionable insights cut remediation efforts significantly.
Suggested Fixes – Beyond sourcing vulnerabilities reported throughout the open source community, we also aggregate their remediation possibilities as offered by the community. Ranging from links to patches to new versions, recommendations for system configuration changes to blocking a specific function, we list all known fixing options for you to choose from.
Automated Workflows – Automatically initiate issue tickets on newly discovered vulnerabilities or recently added vulnerable components and assign action items to ensure proper follow up and remediation of all urgency levels.
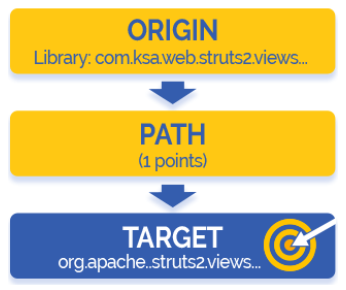
Step III: Continuous Monitoring
Due to the extensive amount of data held by the open source community, and because of open source’s decentralized nature with vulnerability data spread out across multiple databases and security advisories, it is a nearly impossible mission to manually manage all aspects of open source security at scale. Only an automated solution can ensure secure open source usage.
Enforce Policies Automatically Throughout the SDLC – WhiteSource enables you to automatically enforce your security, quality and license compliance policies to block vulnerable or problematic components and get full control over your open source usage.
Setting up automated policies can reduce the number of new components you must manually review by 75-90%, thereby speeding up your software development process and freeing your developers to focus on building great products.
Shift Left & Shift Right Your Open Source Security – To properly tackle open source security, you must combine shift left and shift right methodologies.
Developers can detect vulnerable components before even downloading them based on publicly available data. This process, known as “shifting left” significantly reduces costs and diminishes release delays. Our Web Advisor browser extension helps developers choose the right component the first time around, by alerting on vulnerable components while browsing the web.
The “Shift right” approach is even more critical when it comes to open source, since in many cases vulnerabilities in open source projects are discovered years after the vulnerable version was released. This is why WhiteSource automatically tracks the last inventory of every deployed version and continuously monitors it for newly discovered vulnerabilities, alerting users if one of their historic versions becomes vulnerable.
Integrate Open Source Security into Your CI/CD pipeline – WhiteSource integrates out-of-the-box with all common software development and testing platforms to speed up your software development process and automate the entire process of open source components selection, approval and the detection and remediation of open source security vulnerabilities.
Additional resources about open source security:
- The complete guide for open source security
- Top open source vulnerabilities
- The state of open source vulnerability management
