WhiteSource Software Composition Analysis
How to Choose the Right Solution?
What is SCA and Why is it Important?
SCA tools automatically detect the open source components in your applications and help you manage the different aspects related to your open source usage. Open source components have become an integral part of today’s software development processes. Open source enables companies to build better products, faster. After all, why should you re-invent the wheel when you can just download it from GitHub?
However, it’s still your responsibility to ensure that all of the components in your products are secure and compliant with your company’s policies.
The problem is that verifying that each and every open source component used is secure and complies with your company’s policies has become increasingly complex. That’s because information about open source components is scattered across hundreds of sources with varied levels of credibility, and most databases are not easily searchable.
So how can you get the control you need over your open source usage? Through automation! And this is where Software Composition Analysis (SCA) tools come in.
Governance SCA Solutions & Developers SCA Tools
Most SCA tools fall into one of the two following categories: governance tools which enforce policies in real time and generate reports, or developers’ tools which alert developers on issues within their development environment and provide remediation guidance.
Each category has important benefits, but is strongly focused on its target audience. Only combining both types of tools can provide a solution that addresses the needs of the entire organization. Security, DevOps, and legal teams get the visibility and control that they need, while developers get the tools that they need in order to prevent and fix open source security and compliance issues.
| Governance Solutions | Developers Tools | |
|---|---|---|
| Used by | Management, Security teams, DevOps, Legal teams | Developers |
| Focus | Provide visibility and control over open source risks across the software portfolio | Provide information to help developers avoid and fix vulnerabilities and incompliant open source licenses |
| Features | Reports, real-time alerts, policy enforcement by blocking disallowed open source components | Integrates with native development environments and DevOps tools, provides alerts during early stages of selection and usage of open source components. Actionable insights to help developers easily fix vulnerabilities |
| What’s missing? | It doesn’t alert developers in real-time within their environments on security, quality or compliance issues and doesn’t provide actionable remediation guidance for quicker resolution | It doesn’t provide security and legal teams a solution to enforce policies throughout the SDLC, generate custom reports and get cross-organization visibility |
How Does SCA Support DevSecOps in Your Organization?
DevSecOps, sometimes called DevOps Security or rugged DevOps aims to integrate security into every stage of the development cycle—from planning and design to development, testing, deployment, production, and maintenance. SCA tools can help to enable a DevSecOps culture by helping developers, IT, security and legal teams share responsibility over open source risks.
In the past, management would sometimes enforce open source security standards and block components from use, without the awareness or involvement of development teams. Other times, developers would use their own tools to detect and avoid open source vulnerabilities, with no visibility to other teams or external auditors. Adopting an SCA technology that provides both developer-focused tools and governance solutions, puts developers, IT, security, and legal on the same page.
Breaking Down SCA: 4 Essential Capabilities You Need In Order to Use Open Source Technology Effectively
Which capabilities does your organization need in order to benefit from open source usage, without being exposed to open source security vulnerabilities and legal risk? Below are four essential capabilities, and associated challenges you may run into as you try to implement them.
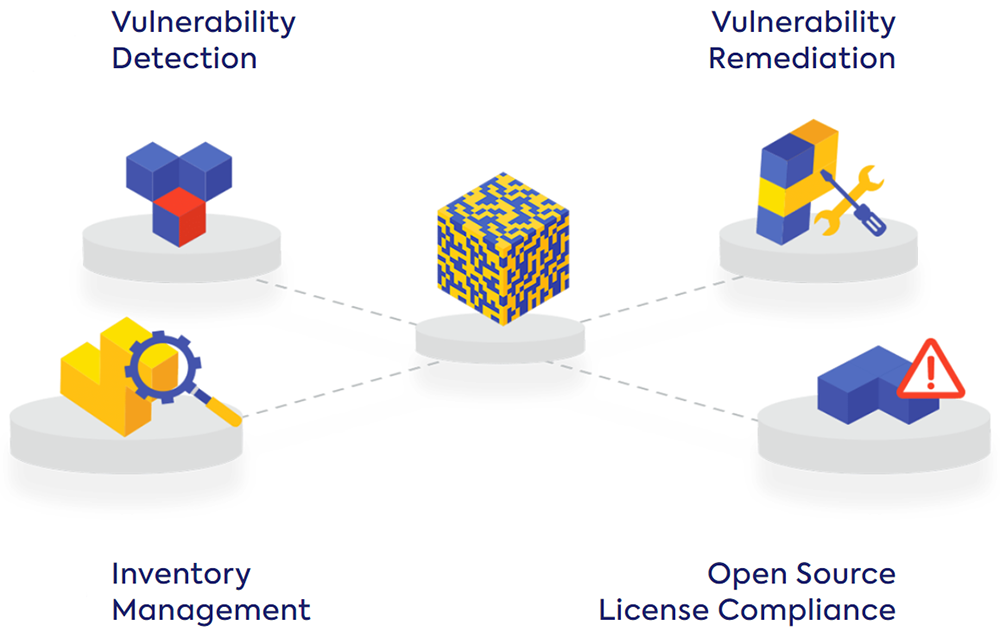
Vulnerability Detection
You must be able to discover open source components with known vulnerabilities as early as possible, when remediation is easiest.
Once a vulnerability is publicly disclosed, you are in a race against hackers to fix it. If you don’t know that you are using a vulnerable open source component, you can’t win this race.
![]()
Challenges
It’s difficult to gather information about open source vulnerabilities
Knowledge about open source vulnerabilities is scattered across multiple sources, many of them are under-the-radar, with different levels of credibility. You need access to all available information to address known vulnerabilities.
False positives
Many SCA tools frequently raise false alarms, making it more difficult to act on the data.
Detection is crucial in every stage of the SDLC
It’s not enough to check at the gate. New components are introduced at every stage of the SDLC.
New vulnerabilities are constantly discovered
New vulnerabilities can be discovered in components that were previously thought to be secure.
Identifying Vulnerable Components: Essential Features
| WhiteSource Offering | |
|---|---|
| Vulnerability data must be comprehensive | – Aggregates dozens of sources: NVD, security advisories, open source project issue trackers. – Rapid assessment of reported vulnerabilities to validate the information. |
| Accuracy | – Guarantees zero false positives. – The patent-pending algorithm matches vulnerabilities with the specific components that they impact, ensuring relevance. |
| Real-Time Alerts | – The components and vulnerabilities DBs are updated multiple times a day. – Immediately provides comprehensive information to prioritize and fix vulnerabilities. |
| Reporting and Auditing | – Offers pre-built reports for all use cases. – Supports R&D, security, legal, management, compliance, due diligence. |
Empowering Open Source Automation with Effective Usage Analysis
Automation of open source vulnerability management and license compliance is critical to solving the challenges we outlined above. However, automated tools have their limitations.
Previous generations of SCA tools could detect open source components and tell organizations that they have vulnerabilities, but were not able to identify the potential impact of those vulnerabilities. This required security and development teams to invest many resources in investigation and response to a large number of vulnerability reports.

Research has shown that of the vulnerabilities discovered, 70-85% were not critical, because the vulnerable open source code was not actually accessed or used by the organization’s proprietary code.
WhiteSource pioneered the next generation of SCA with Effective Usage Analysis. This technology doesn’t just tell you what open source components you have, but also how you use them. It lets you hone in on the 15-30% of open source vulnerabilities that are actually in active use within your product.
It also shows exactly where a vulnerable functionality is referenced within the code, making it much easier for developers to fix vulnerabilities.
Effective Usage Analysis provides automatic prioritization that can reduce remediation efforts, and help teams fix critical vulnerabilities much faster.
The WhiteSource Edge
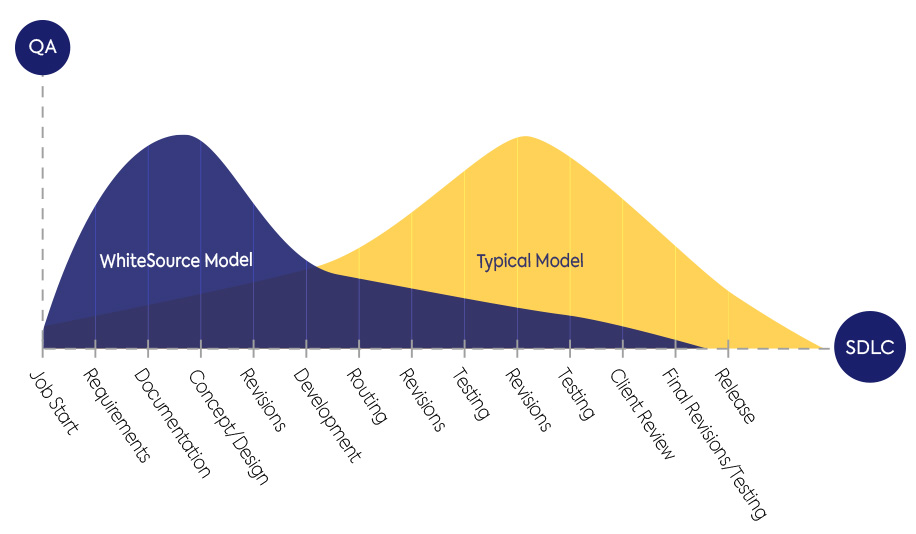
We have covered numerous considerations for selecting an SCA tool for your organization. The bottom line is that you should select an SCA tool that enables you to minimize risk and reduces the effort for all of your teams—from management, legal and security, through ops, developers and QA engineers.
WhiteSource is the leading SCA platform. It helps you minimize risk with the lowest possible effort while fostering a DevSecOps mindset and cooperation across your organization:
![]()
Completeness
A one-stop-shop for all of your open source usage regardless of your languages or environments, including containers and serverless. We also support all groups in your organization: Security, Developers, DevOps, Legal, and Management.
![]()
Prioritization
Focus on what really matters. We help you to prioritize the security vulnerabilities that actually impact your products, and ensure there are no false positives.
![]()
Remediation
Alerts are great, and we also provide the fix. Automatically generate fix pull requests, get direct links to suggested fixes, optimize remediation with full trace analysis and initiate automated workflows including issue tracker integration.
Want to Learn More About WhiteSource?
Simplifying the World of Open Source Usage
We believe the only way to use open source without compromising on security or quality — and without slowing down your developers — is to make this complex process of risk mitigation as simple as possible.
Using open source code should be easy. That’s why we created WhiteSource. Our technology takes care of the heavy lifting that comes with open source usage. We alert you only when something demands your attention, providing you with all the information that you need to make the right choices.
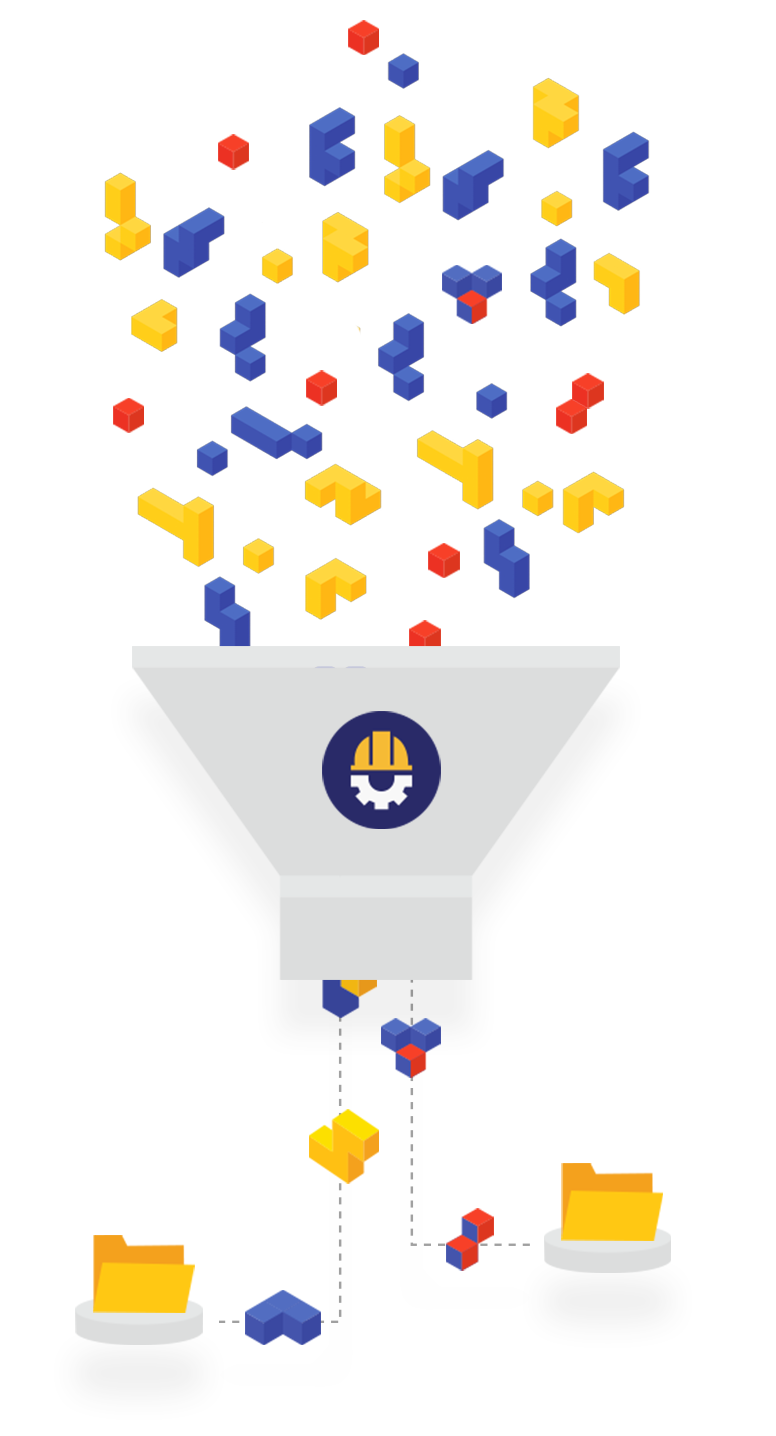
How We Bring Order to Chaos
The WhiteSource platform continuously detects all of the open source components used in your products. It then compares these components against WhiteSource’s database. This database is built by collecting up-to-date information about open source components from numerous sources, including various vulnerability feeds and hundreds of community and developer resources.
The WhiteSource platform is designed for security and compliance professionals, to give managers everything that they need in order to control and manage the open source usage within their organization. It allows them to enforce their policies automatically throughout the SDLC, get real-time alerts on critical issues, and generate up-to-date reports.
It includes a set of tools that fit into the developers’ ecosystem, empowering them to make educated choices, speed up integration, and quickly find and remediate problematic open source components. Because knowledgeable developers make better software.